WEP (which stands for Wired Equivalent Privacy according to Abbreviationfinder) was the first security standard for Wi-Fi networks. Today it is overcome.
The WEP system was designed to provide confidentiality comparable to that of a traditional wired network, it is the acronym for Wired Equivalent Privacy or “Wired Equivalent Privacy”, it is the encryption system included in the IEEE 802.11 standard as a protocol for Wireless networks that allows you to encrypt the information that is transmitted. Provides level 2 encryption, based on the RC4 encryption algorithm that uses 64-bit (40-bit plus 24-bit IV initiation vector) or 128-bit (104-bit plus 24-bit IV) keys. The broadcast messages of wireless networks are transmitted by radio waves, which makes them more susceptible, compared to wired networks, to be captured with relative ease. Presented in 1999.
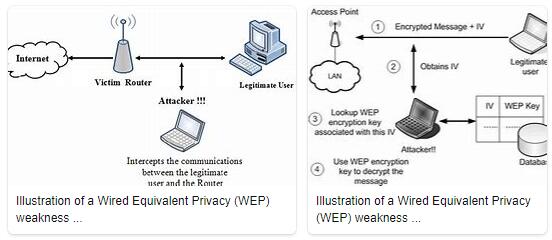
Starting in 2001, several serious weaknesses were identified by crypto analysts. As a consequence, nowadays a WEP protection can be breached with easily accessible software in a few minutes. A few months later the IEEE created the new 802.11i security fix to neutralize the problems. By 2003, the Wi-Fi Alliance announced that WEP had been replaced by Wi-Fi Protected Access (WPA). Finally in 2004, with the ratification of the full 802.11i standard (known as WPA2), the IEEE stated that both WEP-40 and WEP-104 were revoked for flaws in their purpose of providing security. Despite its weaknesses, WEP continues to be used as it is often the first security option presented to users by router configuration tools even though it only provides a level of security that can deter unauthorized use. from a private network, but without providing true protection. It was deprecated as a wireless privacy mechanism in 2004, but it is still documented in the current standard.
WEP is sometimes misinterpreted as Wireless Encryption Protocol.
Definition
WEP (Wired Equivalent Privacy) is the optional security algorithm to provide protection to wireless networks, included in the first version of the IEEE 802.11 standard, kept unchanged in the new 802.11a and 802.11b, with the in order to guarantee compatibility between different manufacturers. WEP is a standard encryption system implemented on the MAC and supported by most wireless solutions. In no case is it compatible with IPSec.
Standard
The IEEE 802.11 standard provides security mechanisms through authentication and encryption processes. In Ad Hoc or Advanced Service Set network mode, authentication can be done through an open system or through a shared key. A network station that receives a request can grant authorization to any station, or only to those included in a predefined list. In a shared key system, only those stations that have an encrypted key will be authenticated.
The 802.11 standard specifies an optional encryption capability called WEP (Wireless Equivalent Privacy); its intention is to establish a level of security similar to that of wired networks. WEP employs RSA Data Security’s RC4 algorithm, and is used to encrypt transmissions made over the air.
Although WLAN systems can resist passive eavesdropping, the only effective way to prevent someone from compromising transmitted data is to use encryption mechanisms. The purpose of WEP is to ensure that WLAN systems have an equivalent level of confidentiality that of LANs wired, by encrypting data that is carried by the signals of Radio. A secondary purpose of WEP is to prevent unauthorized users from accessing WLANs (that is, to provide authentication). This secondary purpose is not explicitly stated in the 802.11 standard, but is considered an important feature of the WEP algorithm. WEP is a critical element to ensure the confidentiality and integrity of data in WLAN systems based on the 802.11 standard, as well as to provide access control through authentication mechanisms. Consequently, most 802.11 compliant WLAN products support WEP as an optional standard feature.
Encryption
WEP uses a secret key shared between a wireless station and an access point. All data sent and received between the station and the access point can be encrypted using this shared key. The 802.11 standard does not specify how the secret key is set, but allows a table to associate a unique key with each station. In general practice, however, the same key is shared between all stations and access points of a given system.
To protect the text Encryption against unauthorized modifications while in transit, WEP applies an integrity check algorithm (CRC-32) to the plaintext, generating an integrity check value (ICV). This integrity check value is concatenated with the plaintext. The integrity check value is, in fact, a kind of fingerprint of the plaintext. The ICV value is added to the ciphertext and sent to the receiver along with the initialization vector. The receiver combines the ciphertext with the key stream to retrieve the plaintext. By applying the integrity algorithm to the plaintext and comparing the output with the received ICV vector, it can be verified that the decryption process has been correct or that the data has been corrupted.
If the two ICV values are identical, the message will be authenticated; in other words, the fingerprints match.
Authentication
WEP provides two types of authentication: an open system, in which all users have permission to access the WLAN, and a shared key authentication, which controls access to the WLAN and prevents unauthorized access to the network. Of the two levels, shared key authentication is the secure mode. It uses a secret key shared between all stations and access points in the WLAN system. When a station tries to connect to an access point, it replies with a random text, which constitutes the challenge. The station must use the copy of its shared secret key to encrypt the challenge text and return it to the access point, in order to authenticate itself. The access point decrypts the response using the same shared key and compares with the previously sent challenge text. If the two texts are identical, the access point sends a confirmation message to the station and accepts it within the network. If the station does not have a password, or if it sends an incorrect response, the access point rejects it, preventing the station from accessing the network.
Shared key authentication works only if WEP encryption is enabled. If not enabled, the system will default to open system (insecure) mode, effectively allowing any station within coverage range of an access point to connect to the network. This creates a window for an intruder to penetrate the system, after which they can send, receive, alter or spoof messages. It is good to ensure that WEP is enabled whenever a secure authentication mechanism is required. Even though shared key authentication is enabled, all wireless stations in a WLAN system can have the same shared key, depending on how the system was installed. In such networks, individual authentication is not possible; all users, including unauthorized ones, who have the shared key will be able to access the network. This weakness can result in unauthorized access, especially if the system includes a large number of users. The more users there are, the greater the likelihood that the shared key may fall into the wrong hands.